Managed IT Services
Elite infrastructure, security-aligned practices, and end-to-end support — Dragon Vault delivers proactive, NIST-aligned IT management to modernize and fortify your operations without disruption.
Onboarding & Environment Stabilization
We begin with a thorough onboarding process that maps your systems, users, vendors, and physical infrastructure into a secure topology...
- Asset tagging, naming conventions, and AD schema audits
- Vendor coordination, ISP failover mapping, Wi-Fi heatmaps
- Encrypted credential vault setup for team-based access
- Initial NIST 800-53 functional checklist assessment
Device Diagnostics & Precision Repair
Whether it’s Windows, macOS, or Linux, our team uses forensic-grade diagnostics and automated testing to resolve bottlenecks fast...
- System imaging, SSD health reports, thermal diagnostics
- Remote repair or dispatch via encrypted RMM channels
- Malware dissection and rollback via system restore sandbox
- Ticket tracking and response time adherence (SLAs available)
Network Architecture & Infrastructure
Your network is your foundation. From Ubiquiti and SonicWall to Meraki and Netgate, we build redundant, monitored, and resilient networks...
- Switch and AP provisioning, VLAN and subnet segregation
- Firewall rulesets, intrusion detection, VPNs & zero-trust architecture
- QoS prioritization for VoIP and mission-critical apps
- 24/7 uptime and failover logging with alerts
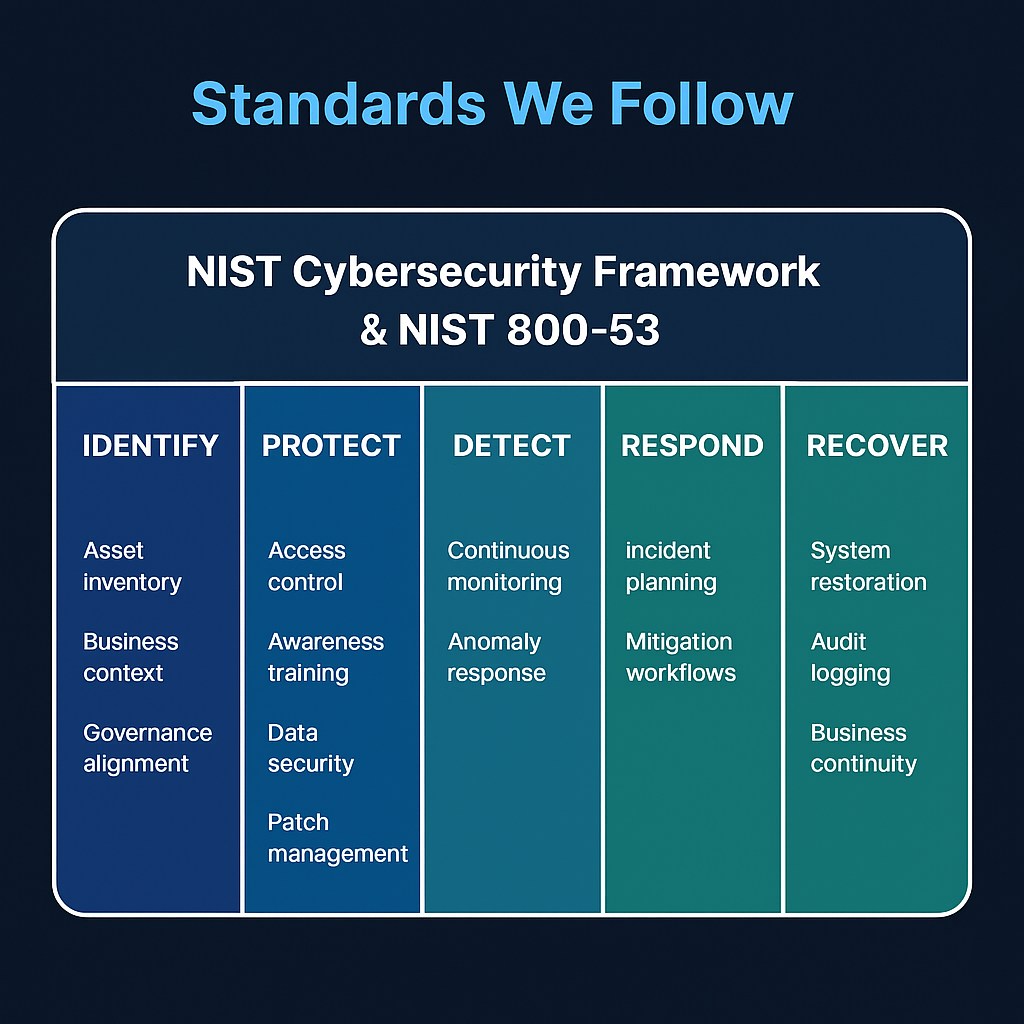
Cybersecurity Standards Alignment
Dragon Vault Technologies aligns operations with the NIST Cybersecurity Framework (CSF) and NIST 800-53 where applicable...
- Identify: Asset inventory, business context, governance alignment
- Protect: Access control, awareness training, data security, patch management
- Detect: Continuous monitoring and anomaly response
- Respond: Incident planning and mitigation workflows
- Recover: System restoration, audit logging, business continuity

Included With Every Engagement
- 24/7 email + remote support access
- Quarterly infrastructure reviews + trend reporting
- Annual disaster recovery simulations
- Dedicated account manager + escalation contacts